Cyber Security
Difference Between VPN and Proxy Server | Proxy vs VPN
In this article, you will find different points of difference between proxy and VPN to clear the concept, working, and other...
What is a Network Security Key
Read out the complete article to learn everything you need to know about network security key Windows 10, 11, or older version...
6 Best Nord VPN Alternative You Should Use in 2022
Best alternatives to Nord VPN ensure online safety at a minimum price (some of them are even free) with a fast connection and...
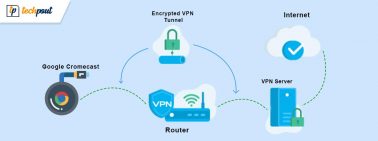
How to Set up VPN on Chromecast
If you want to know how to set up a VPN on Chromecast and surf anonymously, then everything explained in this article will help...
What is Computer Security | Common Computer Security Threats
Read on to get detailed knowledge about computer security, safety risks, and how to protect your computer.Your computer plays...
Is “security@mail.instagram.com” Legit and How to Prevent this on Instagram
Phishing on Instagram has been reported by many users lately. It involves direct messages or emails that look like coming...
When Tech Gets Buggy: How Vulnerabilities can Affect You
Technology is fast paced. Some of the finest examples are the app and system update notifications you receive on your phones and...
7 Tips to Improve Your Employees’ Mobile Security
Cyber-security threats are pervasive nowadays. Business owners are increasingly looking towards mobile-ready solutions for...
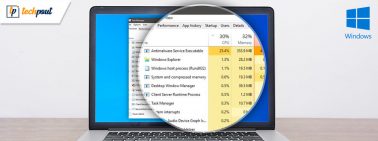
How to Fix ‘Antimalware Service Executable’ High CPU Usage
This hand-on tutorial explains what is the Antimalware Service Executable and various methods to fix its high CPU or memory usage...